 At the beginning of October, Adobe reported a data breach that affected around 3 million customers [1]. In the following weeks, the number rose significantly, but this was just the tip of the iceberg. At the beginning of November a huge dump of the data was published online, containing an eye watering 150 million entries.
At the beginning of October, Adobe reported a data breach that affected around 3 million customers [1]. In the following weeks, the number rose significantly, but this was just the tip of the iceberg. At the beginning of November a huge dump of the data was published online, containing an eye watering 150 million entries.
Various organizations, individuals and companies have analysed this data and have reached the same conclusions: firstly, Adobe’s choice of encryption was extremely poor and secondly, the passwords used by the users were shocking. See the original research by Jeremi Gosney[2], and an excellent article by Paul Ducklin for more information[3].
While most researchers were focusing on cracking the encryption key or criticising Adobe for the poor encryption selection, Corsaire initially did further analysis, focusing on extracting information to help our clients understand the implications of the leak and the lessons that can be learnt from this leak.. We have now decided to publish this advice more widely in the infosec community.
1.1 Weak Password Choice
Looking at Jeremi Gosney’s top 100 list, it is obvious that users are using very weak and simple passwords. While this is no real surprise, the worrying aspect is that many of these weak passwords are associated with corporate email addresses. For example, one global security company is using the generic password ‘123456’ for the account with the email address format of company@company.com
72358235-|–|-company@company.com-|-EQ7fIpT7i/Q=-|-|–
1.2 Password Reuse
Examination of the data reveals users are reusing the same password across multiple accounts, both corporate and personal. For example:
67436532-|–|-jbloggs@company.co.uk-|-VdcYhakfnPioxG6CatHBw==-|-your wife|–
a2342312-|–|-purchasing@company.co.uk-|- VdcYhakfnPioxG6CatHBw==-|-wife|–
72349517-|–|-jbloggs@hotmail.co.uk-|- VdcYhakfnPioxG6CatHBw==-|-wife|–
1.3 Related Accounts
Another piece of information that can be obtained from the reuse of passwords is the ability to link related accounts. In the example below you can track the employment history of J. Bloggs based on his password reuse.
63745506-|–|-jbloggs@acmebank.com-|-nSFKSJFaKERjfsxG6CatHBw==-|-|–
32581259-|–|-joe.bloggs@newcompany.co.uk-|-nSFKSJFaKERjfsxG6CatHBw==-|-|–
23552666-|–|-j.bloggs@getfit.com -|-nSFKSJFaKERjfsxG6CatHBw==-|-|–
19457125-|–|-jbloggs@oldbank.com-|-nSFKSJFaKERjfsxG6CatHBw==-|-|–
Of course, this will be difficult to achieve if the user has chosen a common password.
1.4 Password Hints
As the encryption key is still not publically known, the encrypted passwords cannot be reversed to yield the plaintext password. Unfortunately, the presence of unencrypted password hints supplied by the users allows us to make a very confident guess of the password. A single hint is often not enough information to allow a confident guess, but 10 or more hints for the same password makes the process considerably easier.
In the example below, the encrypted password is:
rI2iugf8+lPioxG6CatHBw==
This is used in 25 different accounts. The associated password hints are:
Favourite element
tl201
Cardiac
Tl u/c
The usual metal
Tl
The rock
201
Seeing all these hints together allows us to make an educated guess that the password is probably ‘Thallium’.
1.5 Recommendations
The main points to take on board from this data leak, (after you have reset all your Adobe account passwords), is that users are the weakest security link in your company. While it is easy to implement and enforce a password policy within the internal corporate environment (via group policies, for example), it’s a very different situation online. You have no control over any particular individuals’ password strength if the online service/site does not enforce it.
This is where user education is vital. Educating your employees in password management best practices is a must and this should be done on a regular basis. Companies must ensure all users not only know and understand the current password policy, but the implications of using weak passwords or reusing passwords between corporate and personal accounts, especially online. In addition to education, providing your users with the ability to generate suitable passwords and store them securely will help (for example, unique password generators and password safe software).
If this has made you nervous and you would like us to examine the leaked data for any accounts related to your company, just get in touch!
Artwork by Michael Gillette
Written by
 Samantha Fielden
Samantha Fielden
Head of Client Management
Corsaire



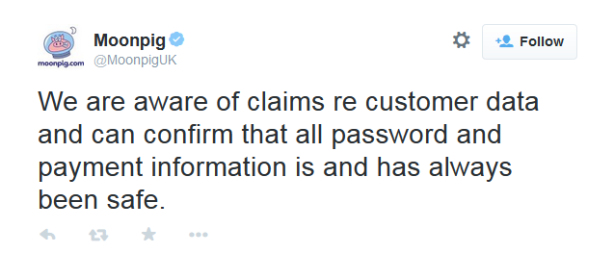 Which has been less than happily received by members of the public, several variations of ‘not quite true’ were uttered in reply.
Which has been less than happily received by members of the public, several variations of ‘not quite true’ were uttered in reply.
 Samantha Fielden
Samantha Fielden